Using containers in software development has led to remarkable improvements in the agility and effectiveness of software deployment. However, it is vital to acknowledge the potential risks associated with containerization, particularly regarding supply chain attacks. A supply chain threat can induce system failures and compromise data security in a clusterized and containerized environment. Therefore, it becomes imperative to address and mitigate such vulnerabilities to ensure the integrity and resilience of the overall system.
This article explores the concept of supply chain attacks and provides insights on mitigating associated risks using Portainer. Portainer empowers you to access secure images effortlessly and offers robust internal authentication for your Kubernetes cluster. Moreover, it presents the opportunity to integrate existing OAuth solutions like Auth0 seamlessly. Upgrade your security posture while leveraging the benefits of Portainer's user-friendly interface and advanced features.
What is a Supply Chain Attack?
A supply chain encompasses various elements such as software, developers, toolings, and infrastructure involved in the construction and deployment of software applications.
When initiating a supply chain attack, cyber attackers identify vulnerabilities in codebases or network protocols. Often, they inject malicious code into codebases after successfully bypassing authentication systems. Supply chain attacks are dangerous as the code containing malicious elements will be utilized during the application's build process, leading to the deployment of compromised applications.
Furthermore, these attacks can also infiltrate your system through third-party components that harbor vulnerabilities. Identifying vulnerabilities within third-party components can prove challenging since you need more visibility into their security measures. It is crucial to remain vigilant regarding the third-party components you employ, promptly addressing any exploitation or detected vulnerabilities. It is advisable to take the necessary steps to safeguard your system against cyber attackers exploiting compromised third-party components to ensure it can resist infiltration and protect its integrity effectively.
How to prevent Supply Chain Attacks
One way to mitigate a supply chain attack is to scan your components, resources, and infrastructure consistently. Scan Docker containers using the docker scan command, and Kubernetes clusters should be examined with various Open Source and commercial software to help identify vulnerabilities within a cluster.
It is imperative to verify and validate every component employed diligently. Putting absolute trust without caution is unwise, as even reputable software companies can fall prey to security breaches. The underlying principle entails downloading the most up-to-date and officially endorsed components that embody extensive trustworthiness and reliability.
Downloading the most recent components and tools ensures your systems remain safeguarded while enjoying optimal performance. By taking this proactive approach, you not only enhance the security of your systems but also defend them against potential threats. Stay ahead of the game and protect your valuable assets. Stay ahead and stay protected! Here are different ways cyber attackers can penetrate your system:
- Stealing hardcoded certificates and secrets to impersonate you and inject malicious code.
- Exploiting vulnerabilities found in code.
Below are a few methods to improve Kubernetes supply chain security:
- Controlling exposure to danger: Regularly scan container images, base images, and dependencies for security vulnerabilities. Apply necessary fixes promptly, as cyber attackers can exploit these weaknesses. Leverage automated scanning tools like to identify any security holes.
- Controlled access: It is crucial to limit access to secrets and enforce stringent auditing and trust of those entrusted with this sensitive information. Only authorized users should be allowed to modify container images, and Kubernetes manifests, ensuring utmost control and integrity.
- Strengthening the container: Configure containers to operate with the lowest possible privileges, ensuring their actions adhere to established security standards.
- System Usage Review: Develop a set of criteria for reviewing and assessing third-party components to ensure their trustworthiness. Exercise caution when sharing data with external vendors, and terminate all data exchanges once the relationship with the third-party component concludes.
How can Portainer help reduce Supply Chain Attacks?
Vulnerabilities like insecure images, container flaws, and weak authentication create opportunities for supply chain attacks. Eliminating these weaknesses is crucial to prevent potentially costly consequences for your company. Recovering from a security breach can be arduous and challenging, underscoring the importance of proactive prevention. Prevent these vulnerabilities by leveraging the solutions provided by Portainer, including:
Easy User Access Control for Kubernetes Clusters and Containers
Kubernetes presents a unique set of challenges, but when considering the broader Cloud Native tooling landscape, it emerges as a formidable and expansive platform. With a team of dedicated developers and administrators, Kubernetes strives to empower seamless service and application facilitation. However, managing and tracking multiple users presents significant challenges. Unregulated access to cluster and container resources exposes the system to unauthorized developers who may exploit and manipulate valuable resources.
Developers play a vital role in the supply chain, but unauthorized access by developers can introduce vulnerabilities. It is crucial to have strict control over who has visibility into cluster resources and operates specific components. Maintaining this level of control is essential to safeguard the integrity and security of the supply chain. Portainer empowers you to bolster user access control by implementing Role-Based Access Control (RBAC) effortlessly. This seamless integration intensifies the security and precision of your system, ensuring enhanced protection and governance.
While it is possible to utilize Kubectl and Docker CLI for implementing RBAC, it may not be the most convenient approach. With Portainer, you can effortlessly implement RBAC using an intuitive GUI, eliminating the need to navigate complex commands or understand intricate terminologies. You must identify the access requirements for individuals and teams within your cluster. With Portainer's user-friendly interface, you can effortlessly create users and groups and assign appropriate roles to them. Below is a screenshot of the Roles you can give users depending on their rights.
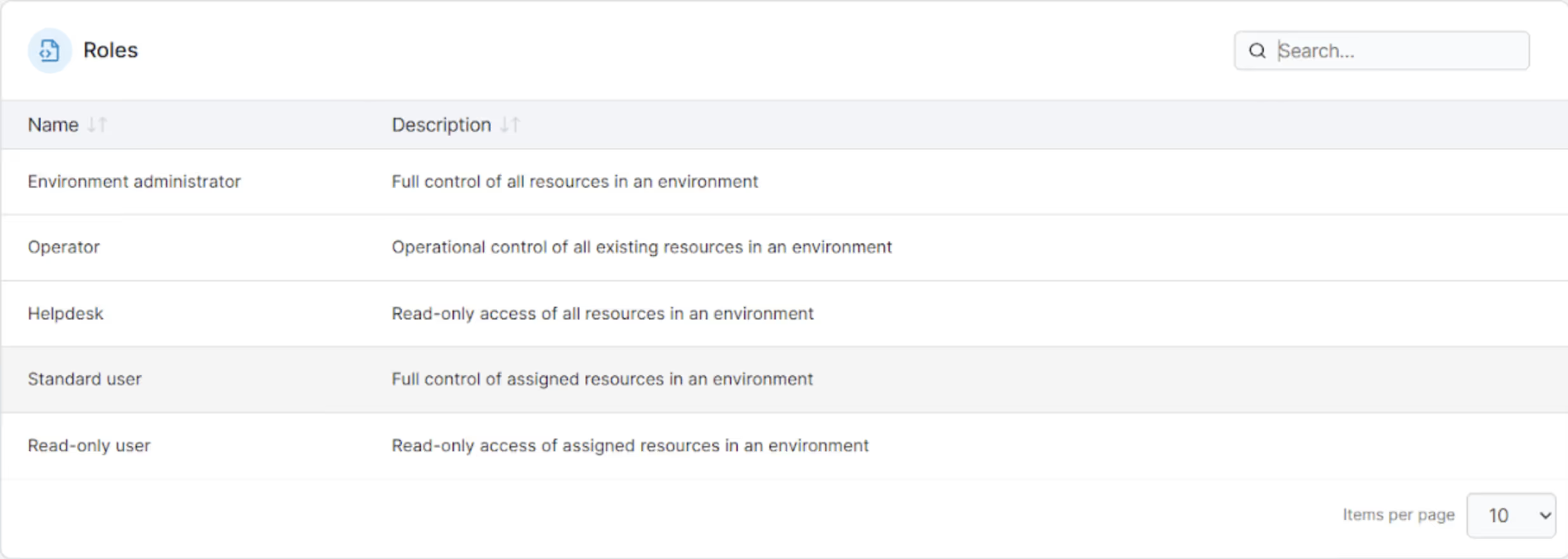
Downloading and Executing Secure Images
Utilizing insecure images can expose vulnerabilities on infrastructure hosts, Industrial IoT devices, and Kubernetes cluster deployments. It is crucial to refrain from downloading images from unofficial sources, as they carry significant security risks. Unofficial images lack proper auditing and verification, amplifying the possibility of exploiting vulnerabilities.
Hence, leveraging DockerHub or a certified container registry for image downloads is crucial. With Portainer, streamlining your developer experience is a breeze. Effortlessly retrieve official images straight from DockerHub or a certified registry, simplifying the process.
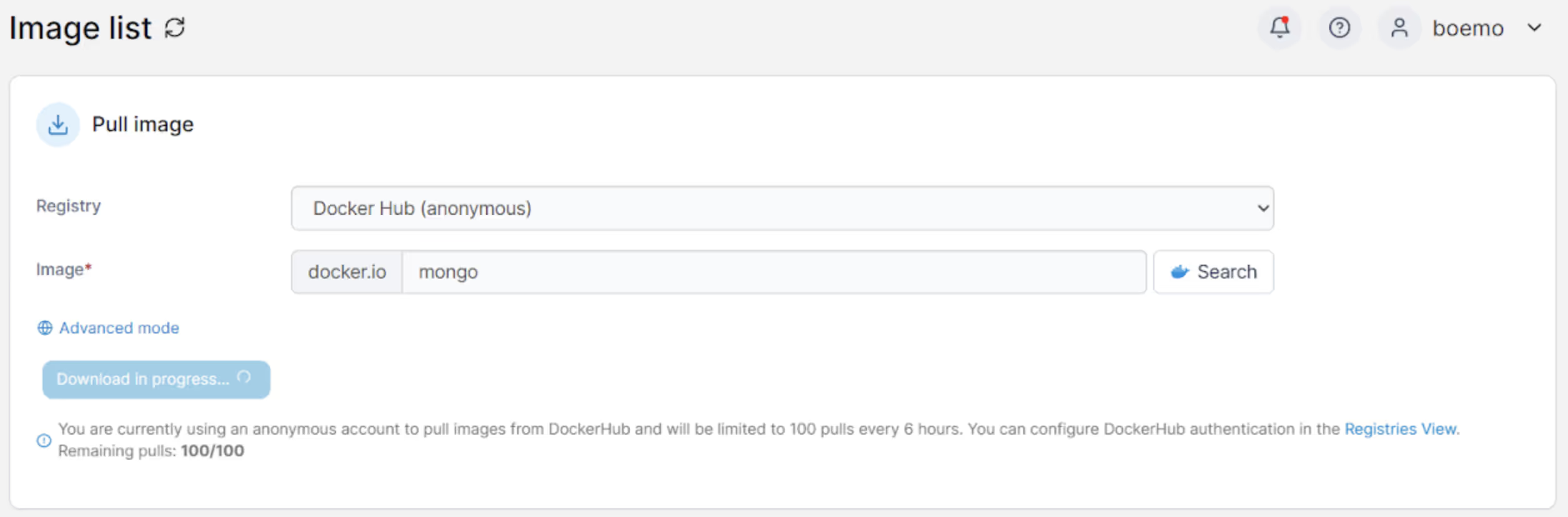
Improving Password Strength and Enabling Third-party OAuth
Securing your Kubernetes and container platform requires careful consideration of authentication providers and fortified credentials. Opt for trusted and well-established solutions that offer robust authentication protocols. Portainer goes beyond its internal authentication feature, providing additional external authentication options to fortify the security of your Kubernetes clusters.
Portainer enhances security by allowing you to integrate your existing OAuth solution into the platform seamlessly. OAuth solutions are trusted because they regularly audit security issues and reduce the need to operate many security credentials and secrets.
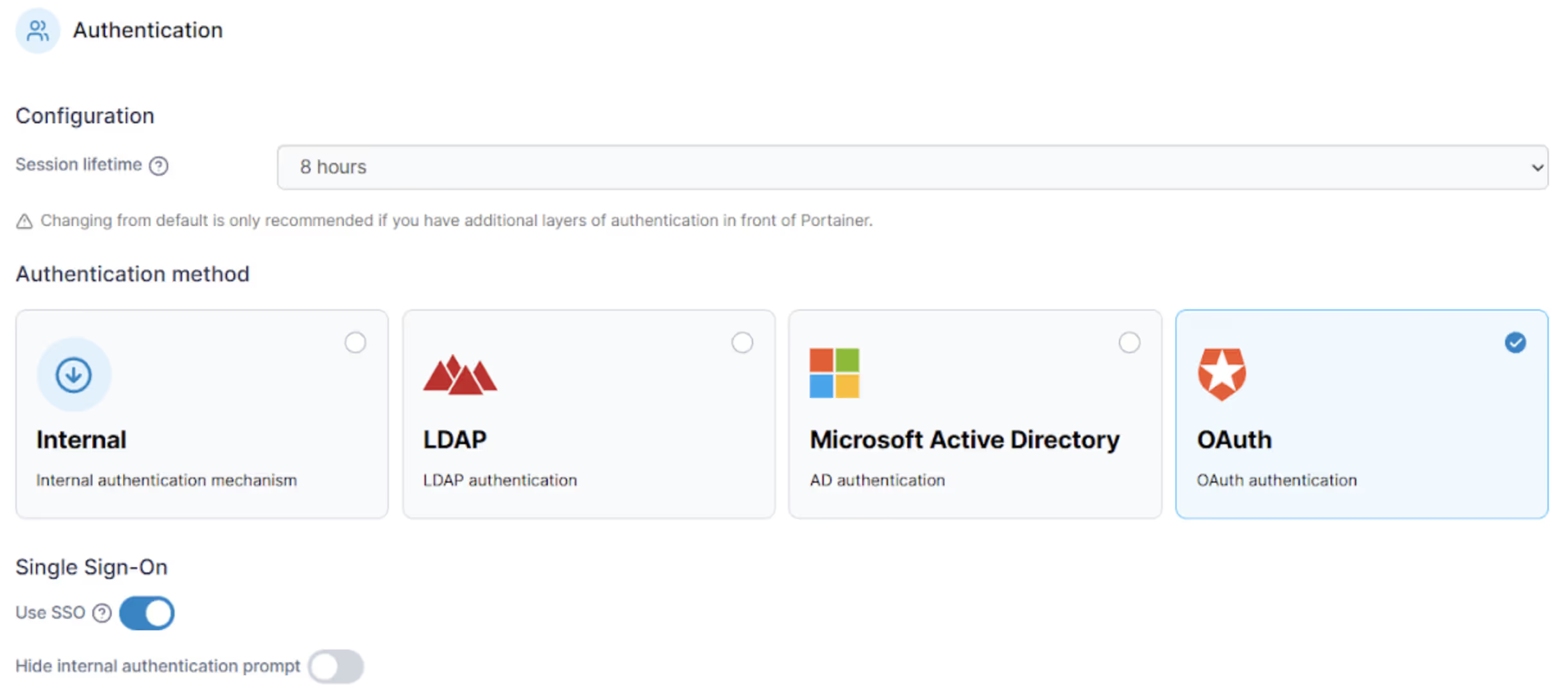
Conclusion
To harness the full potential of containers and tap into the agility and efficiency of Kubernetes, safeguarding against supply chain attacks becomes paramount. It is crucial to protect container environments by implementing robust authentication and RBAC measures. By ensuring secure configurations, we can significantly mitigate vulnerabilities stemming from misconfigurations. Leveraging solutions offered by Portainer and other key players is critical in fortifying your defense against supply chain attacks.
Try Portainer with 3 Nodes Free
If you're ready to start with Portainer Business, 3 nodes free is a great place to begin. If you'd prefer to get in touch with us, we'd love to hear from you!




