Kubernetes RBAC was supposed to bring order to the chaos. Instead of hard-coding permissions or running everything as root, we finally got a structured way to say “this user can do that, but not this.” In theory, it’s elegant: Roles define what actions can be taken, RoleBindings connect those roles to users or groups, and ClusterRoles/ClusterRoleBindings scale this across the cluster. A clean model, right?
The complication starts with inheritance, or rather, the illusion of it. Kubernetes doesn’t have inheritance in the traditional sense. There’s no familiar cascading hierarchy like you’d expect in enterprise systems such as Active Directory. Instead, you have a mesh of bindings that overlap, override, and sometimes unintentionally expand access. A ClusterRole may look like it trickles down into a namespace, but in reality it applies everywhere. A Role feels like it should be scoped and safe, but if a user has another binding elsewhere, the effective permissions are the sum total. Add in ServiceAccounts, impersonation, and custom resources, and suddenly you’re staring at a web of entitlements that nobody fully understands.
And then there are verbs. Kubernetes doesn’t think in terms of “view logs” or “deploy an app,” it thinks in terms of atomic actions like get, list, watch, create, update, patch, and delete. The problem is that there’s no obvious mapping between the task you want to allow and the verbs you need to grant. To exec into a container, you don’t just need get, you often need create. To stream logs, it’s not just get, but list and watch as well. Different resources require different verb combinations, and with custom resources it gets even muddier.
The result is two-fold. First, engineers over-allocate permissions, adding verbs until the task works, often granting far more than necessary. Second, predictability disappears. A developer may be able to do something in one namespace but not another, not because of policy, but because someone forgot a single verb when crafting the Role. Multiply this across dozens of users and multiple clusters, and the whole system becomes nearly impossible to audit or explain.
For platform teams, this leads to three constant headaches:
- Auditing who has what access is painful, since there’s no single view of effective permissions.
- Onboarding and offboarding users is risky, because verbs and bindings interact in non-obvious ways.
- Compliance teams are never satisfied, because you can’t prove what someone can’t do with any confidence.
So, what to do? How do we overcome these misconfiguration risks, audit exposure, and configuration at scale? Portainer RBAC: predictable, auditable, secure.
This is where Portainer takes a fundamentally different approach. Instead of leaving teams to wrestle with verbs, bindings, and inheritance, Portainer defines RBAC in a way that is intentionally simple, auditable, and resistant to misconfiguration.
At its core, Portainer ships with six pre-defined roles: three cluster-scoped, and three namespace-scoped. These roles are hard-set by design, precisely because too much flexibility is what creates risk. Each role already bundles the correct verbs required for the tasks it represents, so you don’t have to play guesswork with get versus list versus watch. A “Namespace Operator” has exactly the verbs needed to manage workloads in their namespace, no more, no less. A “Helpdesk” user can see everything but change nothing, without you needing to craft a custom Role.
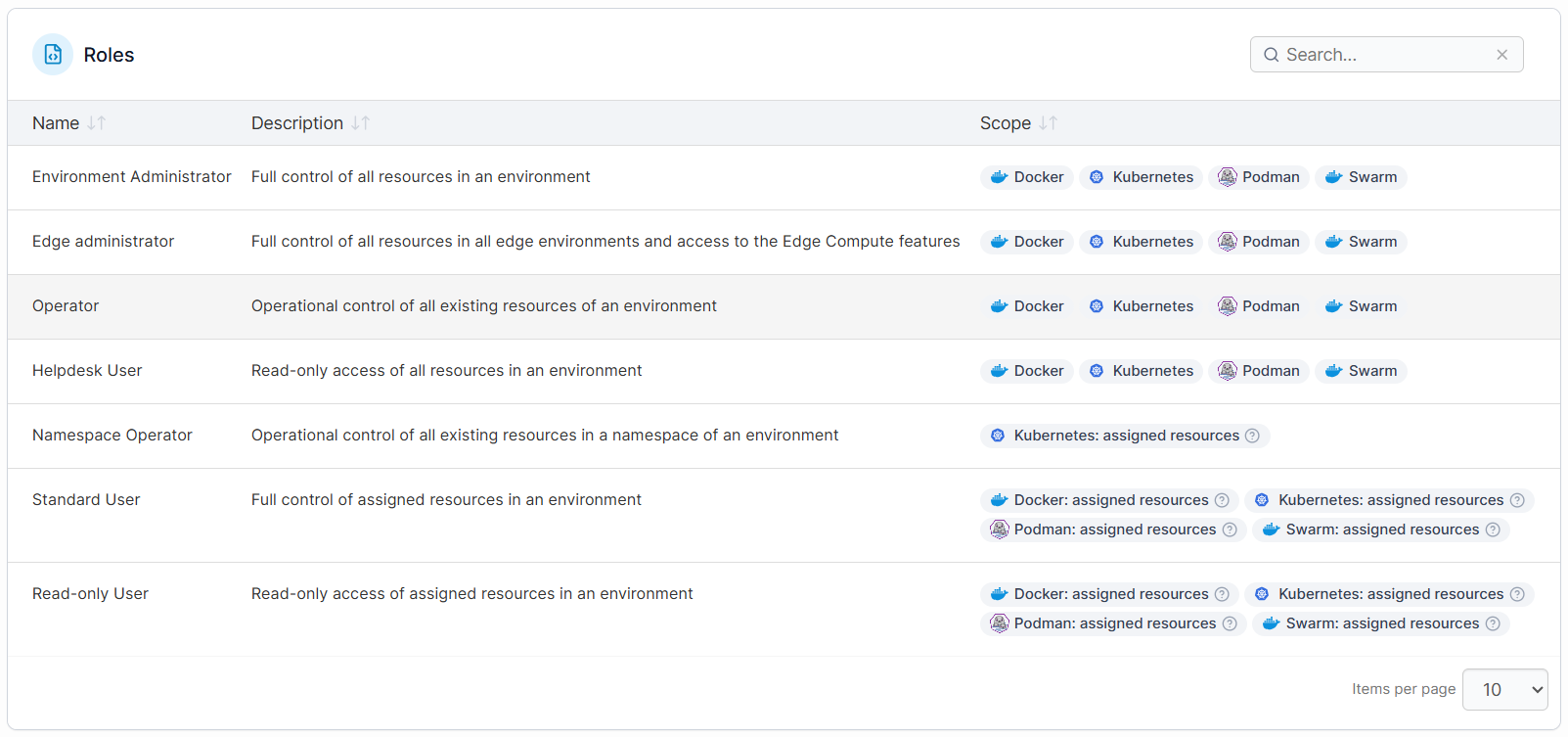
The benefit is predictability. Every Portainer role is well understood, documented, and consistent across clusters. There’s no ambiguity, no additive stacking, and no surprises from forgotten verbs. That makes auditing dramatically easier. Compliance officers see clean, fixed roles; platform teams know that misconfigured YAML won’t accidentally give someone production-level delete rights.
Portainer’s RBAC also scales cleanly across environments. The same six roles apply consistently whether you’re running one cluster or many, eliminating the sprawl and drift that comes with managing Kubernetes RBAC across clusters.
In short, Kubernetes RBAC is powerful but confusing, especially when verbs and bindings combine to create unpredictable privilege. Portainer’s RBAC deliberately avoids that complexity. It’s opinionated, hard-set, and aligned with real-world job functions. That makes it usable by IT generalists, auditable by compliance teams, and secure enough for enterprises.
Because sometimes the most secure system isn’t the one that gives you infinite options, it’s the one that gives you just enough.